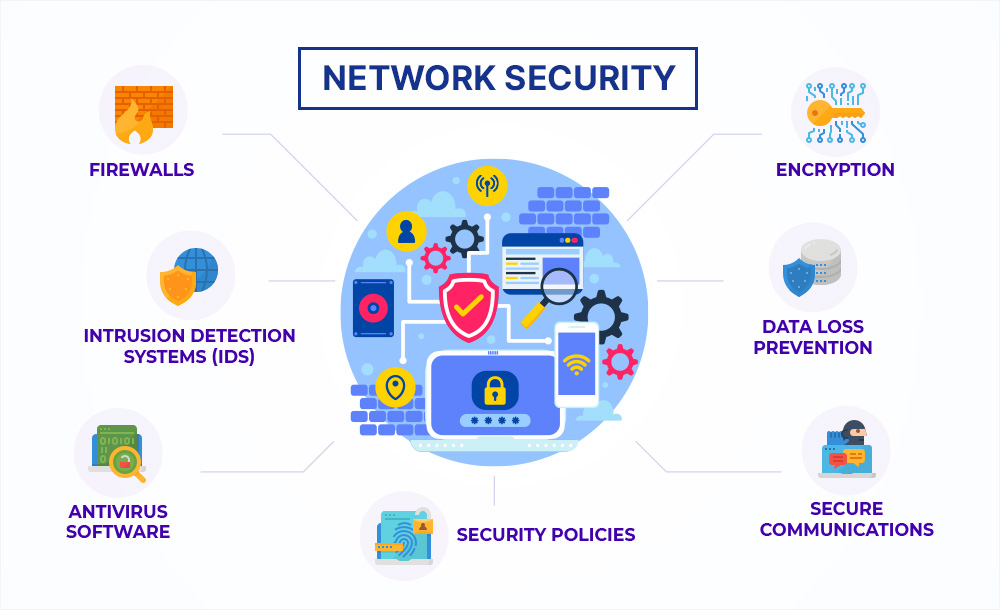
Network & Perimeter Security
Advanced network security solutions and perimeter protection
Advanced Network Security Solutions
Comprehensive protection for your network infrastructure and perimeter
Zero Trust Architecture
Enterprise-grade security implementation with industry best practices
Next-Gen Firewalls deployment
Enterprise-grade security implementation with industry best practices
WAF and IDS/IPS implementation
Enterprise-grade security implementation with industry best practices
Zero Trust Architecture Implementation
Never trust, always verify - comprehensive zero trust security model
Identity Verification
- Multi-factor authentication
- Identity and access management
- Continuous authentication
Device Trust
- Device compliance checking
- Endpoint security posture
- Risk-based access control
Network Segmentation
- Micro-segmentation
- Software-defined perimeters
- Least-privilege access
Next-Generation Firewalls
Deploy advanced firewall solutions that provide deep packet inspection, application awareness, and threat intelligence to protect your network from sophisticated attacks.
Application Control
Granular control over applications and protocols
Threat Intelligence
Real-time threat detection and prevention
SSL Inspection
Deep inspection of encrypted traffic
Security Assessment
Comprehensive evaluation of your current network security posture
Schedule AssessmentWeb Application & Network Protection
Advanced protection for web applications and network infrastructure
Web Application Firewall (WAF)
- OWASP Top 10 protection
- DDoS mitigation
- Bot protection
- API security
IDS/IPS Systems
- Intrusion detection
- Intrusion prevention
- Behavioral analysis
- Automated response
Network Security Infrastructure
Comprehensive security solutions for enterprise networks
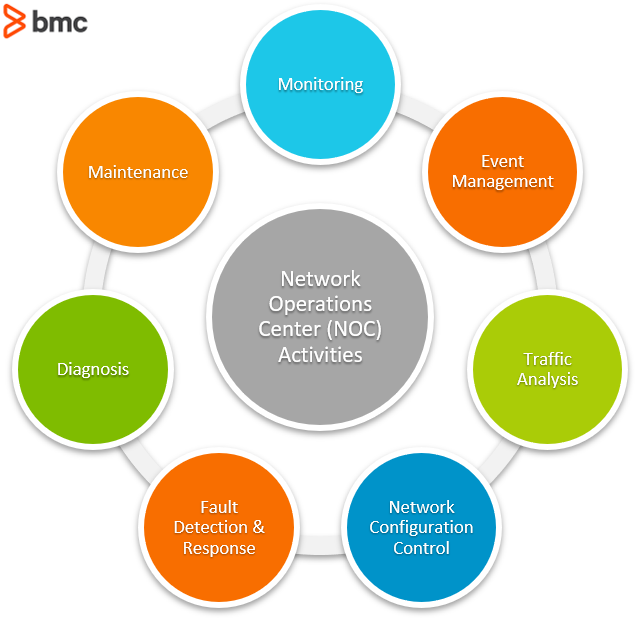
Security Operations Center
24/7 monitoring and threat detection

Cybersecurity Shield
Multi-layered security protection
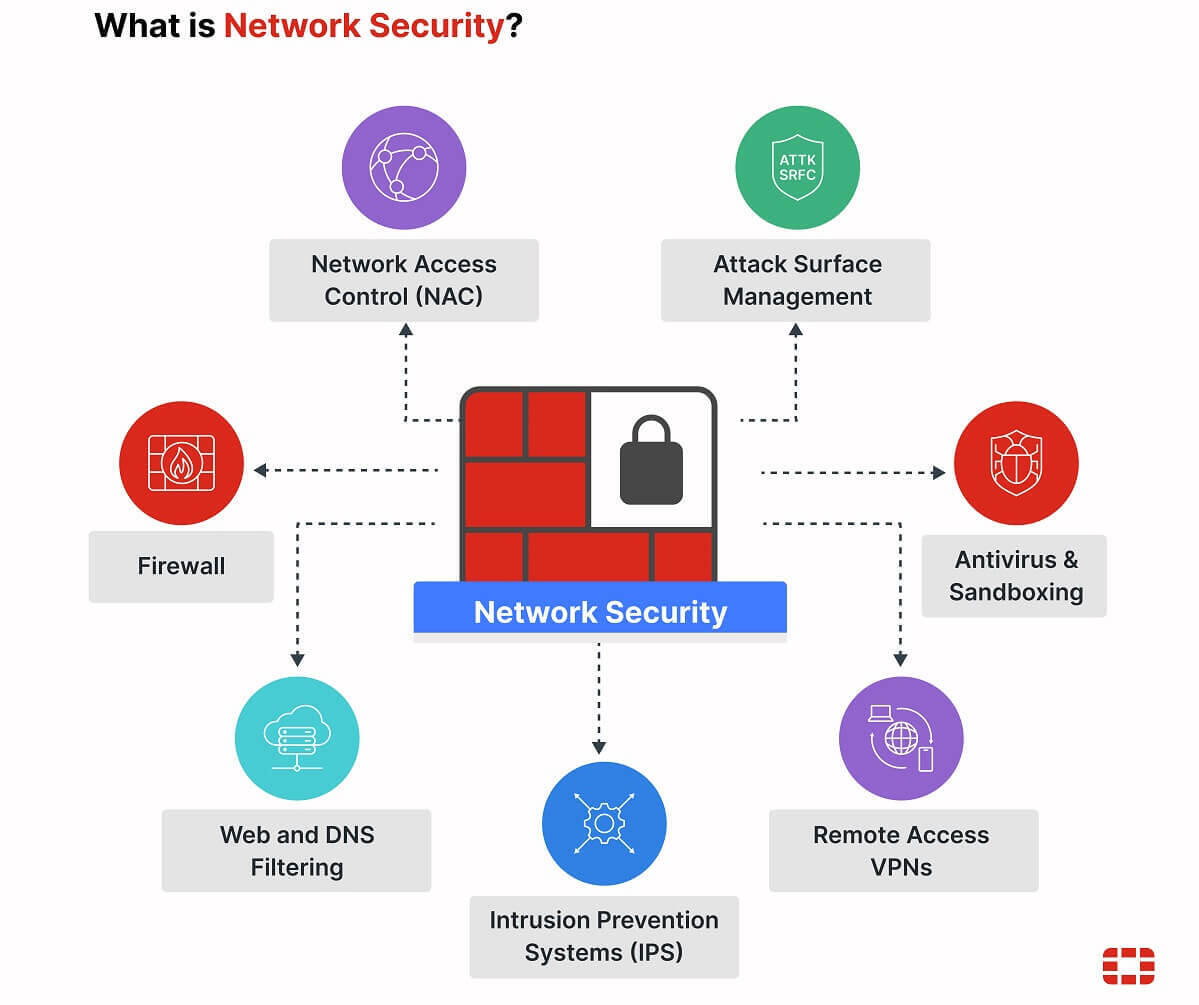
Network Security
Advanced firewall and intrusion detection
Ready to Secure Your Network?
Contact our network security experts to discuss your security requirements and get a customized solution.